Diving into the realm of protecting sensitive data from insider threats, this introduction sets the stage for understanding the critical importance of internal data security measures. From potential risks to real-world examples, this topic sheds light on the impact of insider threats on businesses in a compelling manner.
Exploring common types of insider threats and strategies for prevention, this discussion aims to equip readers with valuable insights to fortify their defenses against data breaches caused by insiders.
Importance of protecting sensitive data from insider threats
Protecting sensitive data from insider threats is essential for organizations to maintain the confidentiality, integrity, and availability of their information assets. Internal threats pose a significant risk as employees or trusted individuals with access to sensitive data can misuse it for personal gain or malicious intent.
Potential risks associated with insider threats
- Unauthorized access: Insiders may abuse their privileges to access confidential data beyond their job responsibilities.
- Data exfiltration: Employees could steal sensitive information and sell it to competitors or use it for personal gain.
- Data manipulation: Insiders might alter or delete critical data, leading to operational disruptions or financial losses.
Impact of data breaches caused by insiders on businesses
Insider threats can have devastating consequences on businesses, including reputational damage, financial losses, legal repercussions, and loss of customer trust. Data breaches caused by insiders can result in regulatory fines, lawsuits, and a decline in business performance. Organizations must implement robust security measures and monitoring systems to detect and prevent insider threats effectively.
Common types of insider threats
Insider threats can come in various forms, ranging from accidental mistakes to intentional malicious actions that put sensitive data at risk. Understanding the different categories of insider threats is crucial in developing effective strategies to protect data.
Negligent Employees
Negligent employees are individuals who inadvertently expose sensitive data due to carelessness or lack of awareness. For example, an employee might leave their computer unlocked, allowing unauthorized access to confidential files. This type of insider threat can compromise data through unintentional actions that violate security protocols.
Malicious Insiders
Malicious insiders are employees who intentionally misuse their access to sensitive data for personal gain or to harm the organization. For instance, a disgruntled employee might steal customer information to sell to competitors or delete important files out of spite.
These insiders pose a significant risk as they have the knowledge and means to bypass security measures and cause serious damage to the organization.
Third-Party Vendors
Third-party vendors with access to internal systems and data can also pose insider threats. While not directly employed by the organization, these vendors can abuse their privileges to compromise sensitive information. For example, a vendor might inadvertently expose confidential data through insecure practices or deliberately leak proprietary information to external parties.
Compromised Accounts
Compromised accounts occur when an insider's credentials are stolen or compromised, allowing unauthorized individuals to access sensitive data. This type of threat can result in data breaches and unauthorized activities that go undetected until it's too late. Hackers or malicious actors may exploit these compromised accounts to steal valuable information or disrupt operations.
Unintentional Insiders
Unintentional insiders are employees who unknowingly contribute to data breaches or security incidents. This could happen through falling victim to phishing scams, clicking on malicious links, or using weak passwords. While their actions are not malicious, unintentional insiders can still create vulnerabilities that threat actors can exploit to gain access to sensitive data.
Strategies for preventing insider threats
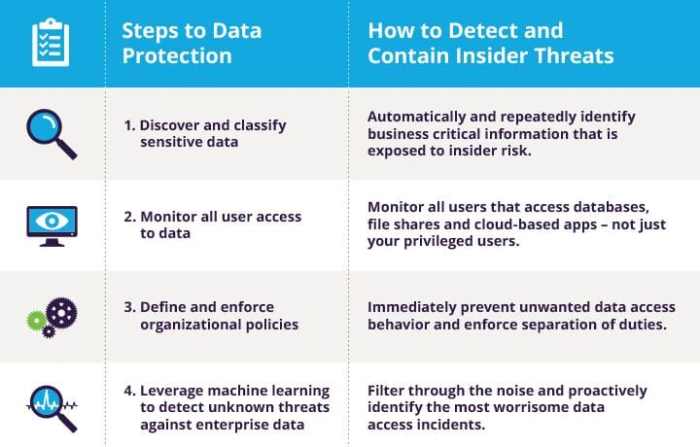
Insider threats can pose a significant risk to an organization's sensitive data. Implementing effective strategies to prevent these threats is crucial in safeguarding valuable information.
Role of Employee Training
Employee training plays a vital role in preventing data breaches caused by insider threats. By educating employees on the importance of data security, recognizing suspicious activities, and following best practices, organizations can empower their staff to act as a line of defense against potential threats.
Importance of Access Control and Monitoring Systems
Access control and monitoring systems are essential components in preventing insider threats. By limiting access to sensitive data based on job roles and implementing real-time monitoring of user activities, organizations can detect unauthorized access or unusual behavior that may indicate a potential insider threat.
Technologies for protecting sensitive data
When it comes to safeguarding sensitive data from insider threats, various technologies play a crucial role in ensuring data security and integrity.
Encryption methods for securing data from insider threats
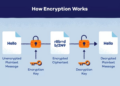
Encryption is a key technology for protecting sensitive data from unauthorized access. By converting data into a coded format that can only be read with the right decryption key, encryption helps prevent insider threats from accessing and exploiting confidential information.
- End-to-end encryption: This method ensures that data is encrypted from the moment it is created until it reaches its intended recipient, making it difficult for insiders to intercept or tamper with the information.
- File-level encryption: Encrypting individual files or documents adds an extra layer of protection, especially for highly sensitive data that needs to be securely stored and shared within an organization.
- Database encryption: Securing databases with encryption helps prevent unauthorized access to critical information stored within the organization's systems, reducing the risk of insider threats compromising sensitive data.
Role of data loss prevention (DLP) tools in safeguarding information
Data loss prevention (DLP) tools are designed to monitor, detect, and prevent unauthorized data transfer or access within an organization. These tools help in identifying and mitigating insider threats by enforcing security policies and preventing sensitive data from being leaked or misused.
- Endpoint DLP solutions: By monitoring and controlling data transfers on endpoints like laptops, smartphones, and USB drives, these tools help prevent insider threats from exfiltrating confidential information.
- Network DLP solutions: Monitoring network traffic and enforcing policies to prevent unauthorized data transmission, network DLP tools play a vital role in safeguarding sensitive data from insider threats.
- Cloud DLP solutions: With the increasing adoption of cloud services, DLP tools tailored for cloud environments help organizations protect sensitive data stored and shared in the cloud from insider threats.
Comparison of different security technologies available to prevent insider threats
Organizations have a range of security technologies at their disposal to combat insider threats effectively. Each technology offers unique features and capabilities to enhance data protection and prevent unauthorized access or misuse.
| Security Technology | Key Features |
|---|---|
| Access Control Systems | Restrict access to sensitive data based on user permissions and roles. |
| Behavior Analytics | Monitor user behavior patterns to detect anomalies and potential insider threats. |
| Security Information and Event Management (SIEM) | Centralize monitoring and analysis of security events to identify and respond to insider threats in real-time. |
| Vulnerability Management | Identify and remediate security vulnerabilities that could be exploited by malicious insiders. |
Outcome Summary
In conclusion, safeguarding sensitive data from insider threats requires a multifaceted approach that combines technology, training, and vigilant monitoring. By staying informed and implementing best practices, organizations can proactively protect their valuable information assets from internal risks.
Top FAQs
What are some best practices for detecting insider threats?
Implementing user behavior analytics, conducting regular security audits, and establishing clear data access policies are key steps in detecting and mitigating insider threats.
How can employee training help in preventing data breaches?
Employee training can raise awareness about security protocols, teach safe data handling practices, and empower employees to recognize and report suspicious activities, thereby reducing the risk of insider threats.
What role do access control and monitoring systems play in preventing insider threats?
Access control ensures that only authorized individuals can access sensitive data, while monitoring systems track user activity to detect any unusual behavior that may indicate a potential insider threat, enhancing overall security measures.

![The 5 Best Laptops for Small Businesses in 2024 [All Budgets]](https://business.blogcristiano.net/wp-content/uploads/2025/11/Top-5-Tech-Gadgets-for-Entrepreneurs-120x86.jpg)