Exploring the importance of multi-factor authentication unveils a crucial layer of security measures that go beyond traditional methods. This comprehensive approach to safeguarding accounts ensures a robust defense against unauthorized access, setting the stage for a compelling discussion on the topic.
Importance of Multi-Factor Authentication
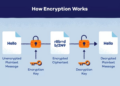
Multi-factor authentication (MFA) is a security process that requires users to provide two or more forms of identification before being granted access to an account or system. This extra layer of security helps ensure that even if one factor is compromised, the account remains protected.
Types of Factors in Multi-Factor Authentication
There are three main types of factors used in multi-factor authentication:
- Something you know, such as a password or PIN.
- Something you have, like a smartphone or security token.
- Something you are, such as biometric data like fingerprints or facial recognition.
Significance of Using Multiple Factors
Using multiple factors for authentication significantly enhances the security of accounts and systems. Here are some key reasons why:
- Increased Security: By requiring multiple factors, MFA makes it much harder for unauthorized users to gain access to sensitive information.
- Reduced Risk of Unauthorized Access: Even if one factor is compromised, the additional factors act as a safeguard against unauthorized access.
- Compliance Requirements: Many industries and organizations are required to implement MFA to comply with data security regulations and protect sensitive data.
- Enhanced User Experience: While adding an extra layer of security, MFA can also streamline the authentication process and provide a more seamless user experience.
Benefits of Multi-Factor Authentication
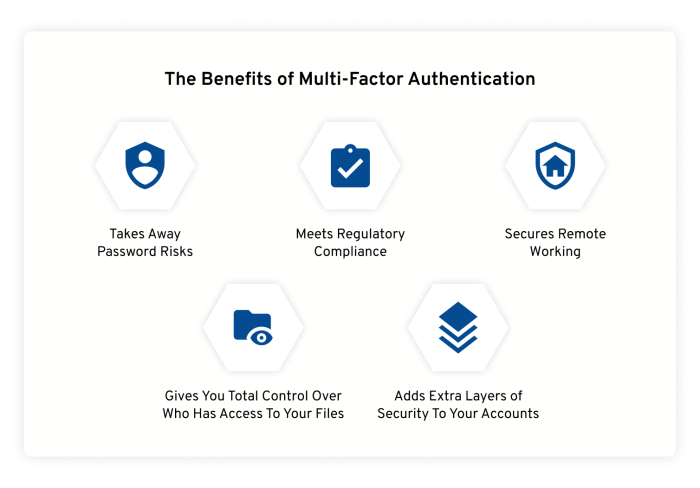
Multi-factor authentication (MFA) offers several benefits in enhancing security and protecting sensitive information from unauthorized access. By requiring multiple forms of verification, MFA significantly reduces the risk of unauthorized entry into systems or accounts.
Enhanced Security with MFA
- MFA adds an extra layer of security beyond just a password, making it harder for cybercriminals to breach accounts.
- By combining something the user knows (password) with something they have (smartphone, token) or something they are (biometric data), MFA creates a robust defense mechanism.
- Even if one factor is compromised, the additional factors provide a safety net, maintaining security.
Comparison of Single-Factor vs. Multi-Factor Authentication
- In single-factor authentication, like password-only systems, the security relies solely on the secrecy of the password.
- However, passwords can be easily stolen, guessed, or hacked, leaving accounts vulnerable to unauthorized access.
- On the other hand, multi-factor authentication significantly increases security by requiring multiple forms of verification.
- Even if a password is compromised, the additional factors in MFA act as barriers to prevent unauthorized access.
Prevention of Unauthorized Access with MFA
- MFA helps prevent unauthorized access by adding layers of protection, making it challenging for attackers to bypass all authentication factors.
- Unauthorized users are less likely to gain entry into systems or accounts protected by MFA, reducing the risk of data breaches and cyber attacks.
- With MFA, organizations can ensure that only authorized individuals with the right credentials can access sensitive information, enhancing overall security posture.
Implementation of Multi-Factor Authentication
When it comes to setting up multi-factor authentication, there are several steps involved to ensure a secure and efficient process. Different technologies are utilized for implementing multi-factor authentication, each with its own set of benefits and challenges. It is important to consider these factors when implementing multi-factor authentication to enhance security measures.
Steps in Setting Up Multi-Factor Authentication:
- Choose the right authentication factors: Decide on which factors to use such as something you know (password), something you have (smartphone), or something you are (fingerprint).
- Select a multi-factor authentication solution: Research and choose a reliable multi-factor authentication solution that aligns with your organization's needs and goals.
- Integrate with existing systems: Ensure seamless integration with your current systems and applications to avoid disruptions in workflow.
- Enforce user enrollment: Encourage users to enroll in multi-factor authentication and provide necessary training and support.
- Regularly monitor and update: Continuously monitor the effectiveness of multi-factor authentication and update as needed to address any vulnerabilities.
Different Technologies Used for Implementing Multi-Factor Authentication:
- One-Time Passwords (OTP): Generated for a single login session and can be sent via SMS, email, or generated by an app.
- Biometric Authentication: Uses unique biological characteristics such as fingerprints, facial recognition, or iris scans for verification.
- Smart Cards: Physical cards with embedded chips that require insertion or contactless interaction for authentication.
- Push Notifications: Alerts sent to a mobile device prompting the user to approve or deny access.
Challenges When Implementing Multi-Factor Authentication:
- User Resistance: Some users may find the additional steps cumbersome and resist using multi-factor authentication.
- Integration Complexity: Integrating multi-factor authentication with existing systems can be challenging and may require additional resources.
- Cost Considerations: Implementing and maintaining multi-factor authentication solutions can incur costs that need to be budgeted for.
- Security Risks: If not implemented correctly, multi-factor authentication can still be vulnerable to attacks such as phishing or social engineering.
Importance in Different Sectors
Multi-factor authentication plays a crucial role in various sectors to enhance security and protect sensitive information. Let's explore its significance in financial institutions, healthcare organizations, and personal accounts/social media platforms.
Financial Institutions
In the financial sector, where transactions involve large sums of money and confidential data, multi-factor authentication is essential. By requiring multiple forms of verification such as passwords, biometrics, and security tokens, financial institutions can significantly reduce the risk of unauthorized access and fraudulent activities.
This extra layer of security helps to safeguard customer accounts, prevent identity theft, and ensure compliance with industry regulations.
Healthcare Organizations
Healthcare organizations deal with highly sensitive patient information, making them a prime target for cyber attacks. Multi-factor authentication is crucial in this sector to protect electronic health records, maintain patient confidentiality, and prevent data breaches. By implementing multi-factor authentication protocols, healthcare organizations can strengthen their defense against cyber threats and safeguard patient privacy.
Personal Accounts and Social Media Platforms
For individuals, using multi-factor authentication for personal accounts and social media platforms adds an extra layer of protection against unauthorized access. By combining something you know (password) with something you have (security code sent to your phone), multi-factor authentication reduces the risk of hacking and identity theft.
This security measure is particularly important in today's digital age, where cyber threats are prevalent, and personal information is increasingly at risk.
Final Wrap-Up
In conclusion, the adoption of multi-factor authentication emerges as a pivotal strategy in fortifying digital security across various sectors. By incorporating multiple factors to verify identities, organizations and individuals alike can mitigate risks and bolster protection against potential threats.
FAQ Insights
How does multi-factor authentication enhance security?
Multi-factor authentication adds an extra layer of security beyond passwords by requiring additional verification methods, reducing the risk of unauthorized access.
What are some challenges when implementing multi-factor authentication?
Challenges may include user resistance to new security measures, compatibility issues with existing systems, and the need for adequate user training.

![The 5 Best Laptops for Small Businesses in 2024 [All Budgets]](https://business.blogcristiano.net/wp-content/uploads/2025/11/Top-5-Tech-Gadgets-for-Entrepreneurs-120x86.jpg)