Exploring the realm of ransomware attacks, this article delves into effective strategies and essential practices to safeguard individuals and organizations against cyber threats. From understanding the mechanics of ransomware to implementing robust prevention measures, this guide offers valuable insights to fortify your digital defenses.
Introduction to Ransomware Attacks
Ransomware attacks have become a significant threat to both individuals and organizations in recent years. These malicious attacks involve encrypting data and demanding a ransom for its release, causing financial losses and data breaches.
How Ransomware Attacks Work
Ransomware attacks typically enter a system through phishing emails, malicious attachments, or compromised websites. Once the ransomware infiltrates a device or network, it encrypts files and demands payment in exchange for decryption keys.
- Ransomware is often spread through phishing emails that trick recipients into clicking on malicious links or downloading infected attachments.
- Some ransomware strains exploit software vulnerabilities to infect systems without user interaction.
- Once the ransomware encrypts files, it displays a ransom note demanding payment in cryptocurrency to unlock the data.
The Importance of Preventing Ransomware Attacks
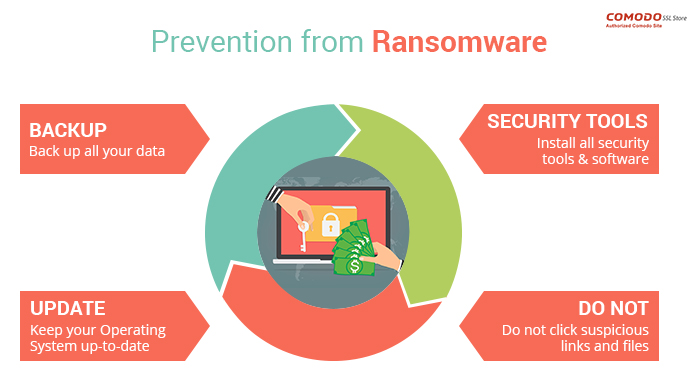
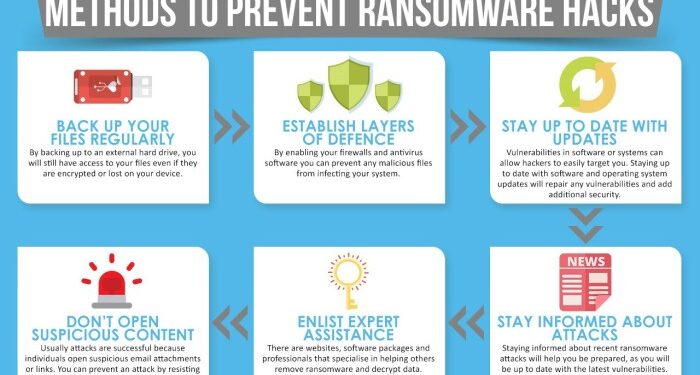
Preventing ransomware attacks is crucial to safeguarding sensitive data, protecting financial assets, and maintaining business continuity. By implementing robust cybersecurity measures and employee training, individuals and organizations can reduce the risk of falling victim to ransomware attacks.
- Preventing ransomware attacks can prevent costly ransom payments and potential legal consequences.
- Protecting against ransomware helps maintain trust with customers and partners by ensuring the security of their data.
- Implementing preventive measures can help avoid downtime and data loss that could impact operations and reputation.
Best Practices for Ransomware Prevention

Ransomware attacks can have devastating consequences for individuals and organizations. Implementing proper security measures is crucial in protecting against these threats. Here are some best practices to prevent ransomware attacks:
Essential Security Measures
- Install and regularly update antivirus software to detect and block ransomware.
- Enable firewalls to monitor and control incoming and outgoing network traffic.
- Implement strong password policies and use multi-factor authentication for added security.
- Educate employees on cybersecurity best practices and how to identify phishing attempts.
- Restrict user access to sensitive data and limit administrative privileges.
Role of Software Updates and Patches
Regularly updating software and applying security patches is crucial in preventing ransomware attacks. Outdated software often contains vulnerabilities that attackers can exploit to gain access to systems. By keeping software up-to-date, organizations can reduce the risk of falling victim to ransomware.
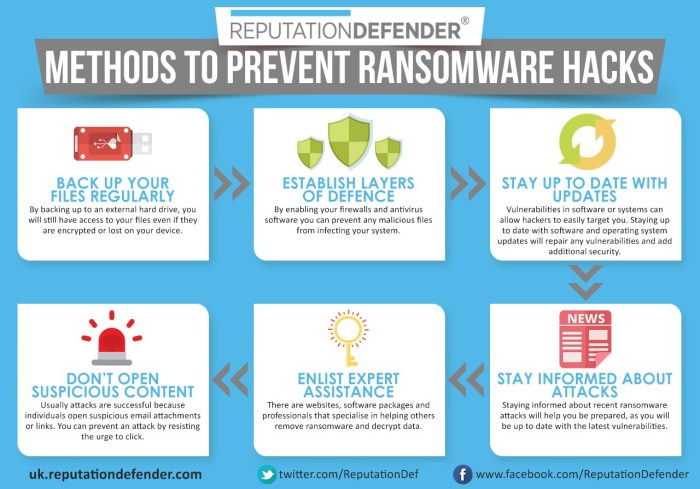
Significance of Data Backups and Disaster Recovery Plan
Creating regular backups of important data is essential in mitigating the impact of a ransomware attack. In the event of an attack, having backups allows organizations to restore their data without having to pay the ransom.
- Store backups offline or in a secure cloud environment to prevent them from being compromised by ransomware.
- Test backups regularly to ensure they are viable for restoration in case of an emergency.
- Develop a comprehensive disaster recovery plan that Artikels steps to be taken in the event of a ransomware attack, including communication protocols and recovery procedures.
Employee Training and Awareness
Employee training and awareness play a crucial role in preventing ransomware attacks. Educating employees about ransomware threats and the importance of cybersecurity is essential in safeguarding the organization's data and systems.
Importance of Employee Awareness
- Employees are often the first line of defense against ransomware attacks, making it vital for them to be aware of potential threats.
- Understanding how ransomware works and the common tactics used by cybercriminals can help employees recognize suspicious activities and emails.
- By fostering a culture of cybersecurity awareness, employees can actively contribute to the overall security posture of the organization.
Tips for Conducting Security Awareness Training
- Regularly conduct training sessions to educate employees on the latest ransomware trends, prevention techniques, and best practices.
- Simulate phishing attacks to test employees' responses and provide real-time feedback on how to improve their cybersecurity awareness.
- Encourage employees to report any suspicious emails or activities promptly to the IT department for further investigation.
- Ensure that training materials are easily accessible and understandable, catering to employees at all levels of technical proficiency.
Network Security Measures
Implementing robust network security measures is crucial in preventing ransomware attacks. By securing your network infrastructure, you can significantly reduce the risk of unauthorized access and data breaches.
Implement Network Segmentation
Network segmentation involves dividing a network into smaller, isolated segments to limit the spread of ransomware in case of a breach. This strategy helps contain and mitigate the impact of an attack, preventing it from spreading across the entire network.
- Segmenting networks can prevent lateral movement of ransomware within the network.
- By isolating critical systems and data, you can minimize the potential damage caused by a ransomware attack.
- Implementing network segmentation also enhances network performance and security by creating barriers between different network components.
Use Firewalls, Intrusion Detection Systems, and Endpoint Security Solutions
Firewalls, intrusion detection systems (IDS), and endpoint security solutions play a crucial role in safeguarding your network from ransomware threats.
- Firewalls act as a barrier between your internal network and external threats, filtering incoming and outgoing traffic to block malicious activities.
- Intrusion detection systems monitor network traffic for suspicious behavior or known ransomware signatures, alerting administrators to potential threats.
- Endpoint security solutions protect individual devices such as computers and mobile devices from ransomware attacks, detecting and blocking malicious software before it can execute.
Restrict User Access Privileges
Limiting user access privileges is essential in reducing the risk of ransomware attacks by restricting the ability of users to access sensitive data and systems.
- Grant users access only to the resources necessary for their job roles, minimizing the exposure of critical data to potential threats.
- Implement the principle of least privilege, ensuring that users have only the minimum level of access required to perform their tasks effectively.
- Regularly review and update user access permissions to align with business needs and security best practices, reducing the likelihood of unauthorized access.
Incident Response Planning
Effective incident response planning is crucial in mitigating the impact of ransomware attacks. Regular testing and updating of incident response procedures are essential to ensure preparedness in the event of an attack. Developing a comprehensive incident response strategy involves several key components.
Key Components of an Effective Incident Response Plan
- Establishing an incident response team with clearly defined roles and responsibilities.
- Creating a detailed incident response plan outlining procedures to be followed in case of a ransomware attack.
- Implementing communication protocols to ensure timely and effective coordination during an incident.
- Identifying and securing critical assets to prevent further damage or data loss.
- Engaging legal and regulatory experts to address any legal implications of a ransomware attack.
Importance of Regular Testing and Updating
- Regular testing helps identify weaknesses in the incident response plan and allows for necessary adjustments to be made.
- Updating procedures based on lessons learned from testing and real-world incidents ensures that the plan remains effective and relevant.
- Continuous training and drills help keep the incident response team prepared and responsive in high-pressure situations.
Steps for Developing a Comprehensive Incident Response Strategy
- Conduct a risk assessment to identify potential threats and vulnerabilities.
- Define clear objectives and priorities for the incident response plan.
- Establish communication channels and escalation procedures for reporting and responding to incidents.
- Document response procedures, including containment, eradication, and recovery steps.
- Coordinate with external partners, such as law enforcement and cybersecurity experts, for additional support and guidance.
Last Word
In conclusion, by staying vigilant, educating employees, fortifying network security, and developing a comprehensive incident response plan, you can significantly reduce the risks of falling victim to ransomware attacks. Remember, prevention is key in the ever-evolving landscape of cybersecurity threats.
Stay informed, stay prepared, and stay secure.
Q&A
How often should data backups be performed?
Regular data backups should be performed daily or at least on a weekly basis to ensure minimal data loss in case of a ransomware attack.
What role do software updates play in preventing ransomware attacks?
Software updates are crucial as they often contain security patches that address vulnerabilities exploited by ransomware. Regular updates help strengthen your defenses.
Why is employee training important in ransomware prevention?
Employee training is vital as human error is a common entry point for cyber attacks. Educating employees about ransomware threats and best practices can significantly reduce risks.

![The 5 Best Laptops for Small Businesses in 2024 [All Budgets]](https://business.blogcristiano.net/wp-content/uploads/2025/11/Top-5-Tech-Gadgets-for-Entrepreneurs-120x86.jpg)