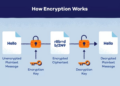
Delving into the intricate world of data security, one crucial element stands out: encryption. This powerful tool serves as a shield, protecting sensitive information from prying eyes and potential threats. As we navigate the digital landscape, understanding the role of encryption is paramount in safeguarding our valuable data.
As we explore the nuances of encryption and its impact on data security, a clearer picture emerges of its significance in today's interconnected world.
Importance of Encryption in Data Security
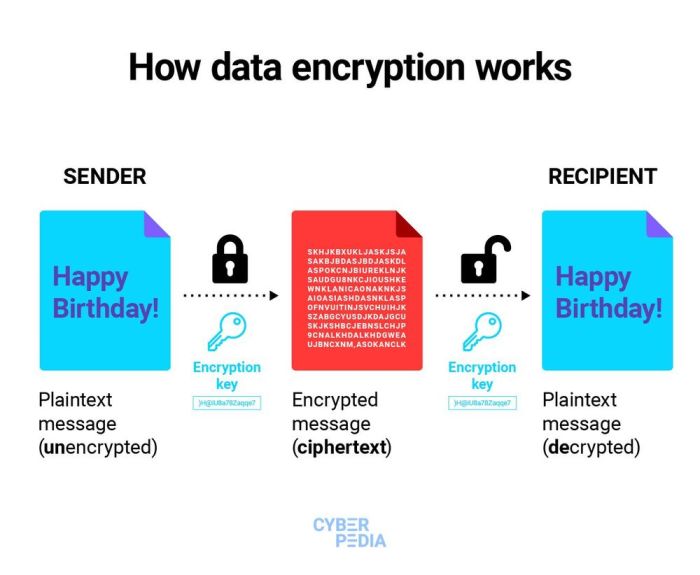
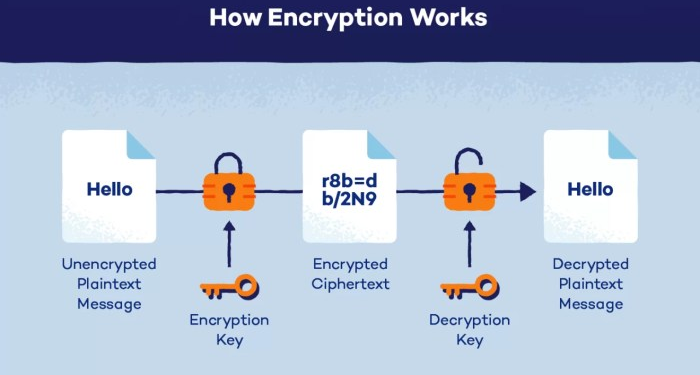
Encryption plays a crucial role in safeguarding sensitive information from unauthorized access and potential breaches. By converting data into a secure code that can only be accessed with the right decryption key, encryption ensures that even if data is intercepted, it remains unreadable and protected.
Preventing Data Exposure
- One notable example of a data breach where encryption could have prevented data exposure is the Equifax breach in 2017, where hackers accessed personal information of over 147 million people, including social security numbers and credit card details. Had the data been encrypted, even if the hackers gained access to the data, they would not have been able to decipher it without the encryption keys.
- Another example is the Yahoo breach in 2013, where 3 billion user accounts were compromised. If the data stored on Yahoo's servers had been encrypted, the impact of the breach could have been significantly minimized, as the stolen data would have been unreadable without the encryption keys.
Compliance with Data Protection Regulations
- Encryption also plays a vital role in ensuring compliance with data protection regulations such as the General Data Protection Regulation (GDPR) and the Health Insurance Portability and Accountability Act (HIPAA). These regulations mandate the protection of sensitive data through encryption to prevent unauthorized access and data breaches.
- Failure to encrypt sensitive data can result in hefty fines and legal consequences for organizations, highlighting the importance of encryption in maintaining compliance with data protection laws.
Types of Encryption Algorithms

Encryption algorithms play a crucial role in safeguarding data by converting it into a secure format that can only be accessed with the right decryption key. There are various types of encryption algorithms used in data security, each with its own characteristics and strengths.
Common Encryption Algorithms
- Advanced Encryption Standard (AES): AES is a symmetric encryption algorithm widely used for securing sensitive data. It offers a high level of security and efficiency, making it a popular choice for protecting information.
- Rivest-Shamir-Adleman (RSA): RSA is an asymmetric encryption algorithm that utilizes public and private key pairs for encryption and decryption. It is commonly used for securing communications over the internet.
- Triple Data Encryption Standard (3DES): 3DES is a symmetric encryption algorithm that applies the Data Encryption Standard (DES) cipher three times to enhance security. Although it's slower than AES, it is still used in certain applications.
Symmetric vs. Asymmetric Encryption
Symmetric encryption uses a single key for both encryption and decryption, making it faster and more efficient. However, the challenge lies in securely sharing this key with the intended recipient. On the other hand, asymmetric encryption uses a pair of keys – public and private – to encrypt and decrypt data.
While it's slower than symmetric encryption, it eliminates the need to share a secret key.
Significance of Key Length
The key length plays a critical role in determining the strength of encryption. A longer key length increases the complexity of breaking the encryption, thus enhancing security. For example, AES-256 uses a 256-bit key, making it significantly more secure than AES-128, which uses a 128-bit key.
Implementation of Encryption in Different Systems
Encryption plays a crucial role in ensuring data security across various operating systems and platforms. Let's explore how encryption is integrated into different systems, the challenges faced, and best practices for implementation.
Integration into Operating Systems
Encryption is an essential component of data security in operating systems such as Windows, macOS, and Linux. These systems provide built-in encryption tools that allow users to secure their sensitive information and communications.
- Windows: BitLocker is a popular encryption tool in Windows that helps users encrypt their drives and protect data from unauthorized access.
- macOS: FileVault is the encryption feature in macOS that enables users to encrypt their entire system drive for enhanced security.
- Linux: Linux systems often use tools like LUKS (Linux Unified Key Setup) for disk encryption, ensuring data protection on various distributions.
Challenges and Best Practices in Cloud-Based Systems
Implementing encryption in cloud-based systems presents unique challenges due to the distributed nature of data storage and processing. It is essential to follow best practices to ensure data confidentiality and integrity in cloud environments.
- Challenges: Key management, data residency compliance, and scalability are some of the challenges faced when implementing encryption in cloud systems.
- Best Practices: Use strong encryption algorithms, implement secure key management practices, regularly update encryption protocols, and conduct security audits to maintain data protection in the cloud.
Encryption Protocols for Securing Communication Channels
Encryption protocols like HTTPS, SSL (Secure Sockets Layer), and TLS (Transport Layer Security) are used to secure communication channels and ensure data privacy during transmission over networks.
- HTTPS: HyperText Transfer Protocol Secure encrypts data exchanged between a web server and a browser, protecting sensitive information from eavesdroppers.
- SSL/TLS: SSL and TLS protocols establish secure connections between clients and servers, encrypting data to prevent unauthorized access and tampering.
Encryption Key Management

Effective encryption key management is crucial for maintaining the security of encrypted data. Without proper key management, even the strongest encryption algorithms can be compromised.
Importance of Secure Key Management
- Secure key management ensures that only authorized individuals can access encrypted data.
- It helps in protecting sensitive information from unauthorized access, ensuring data confidentiality.
- Proper key management also plays a vital role in data integrity, preventing data tampering or unauthorized modifications.
Key Rotation Strategies and Impact on Data Security
- Key rotation involves changing encryption keys at regular intervals to reduce the risk of a compromised key leading to a data breach.
- Regular key rotation enhances security by limiting the window of opportunity for attackers to decrypt data using a stolen key.
- However, key rotation strategies must be carefully planned to avoid disruptions in data access and ensure seamless encryption and decryption processes.
Key Escrow and its Role in Data Recovery Processes
- Key escrow is a process where a trusted third party holds a copy of encryption keys to be used for data recovery in case of key loss or unavailability.
- It provides a backup solution to recover encrypted data when the original encryption key is lost or compromised.
- Key escrow can be beneficial in scenarios where key management issues lead to data loss, allowing organizations to regain access to their encrypted data.
Final Wrap-Up
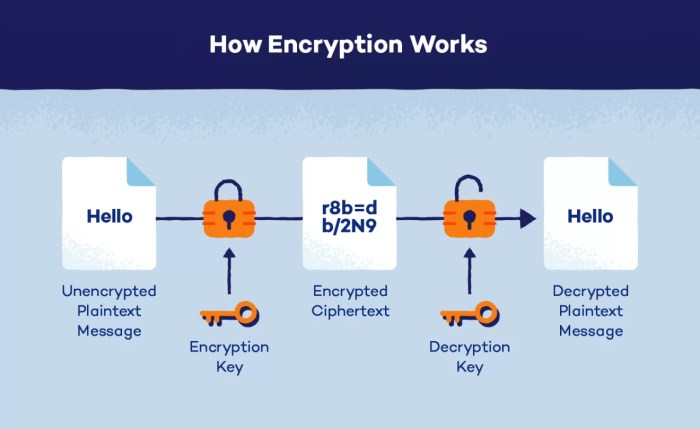
In conclusion, the intricate dance between encryption and data security unveils a crucial partnership that underpins our digital existence. As we continue to evolve in the realm of cybersecurity, embracing encryption as a fundamental pillar is not just a choice but a necessity for safeguarding our most valuable assets.
Answers to Common Questions
What is the primary purpose of encryption in data security?
Encryption plays a vital role in securing sensitive information by converting it into a coded format that can only be accessed with the appropriate decryption key.
How does encryption assist in compliance with data protection regulations?
Encryption helps organizations adhere to data protection regulations by ensuring that sensitive data is stored and transmitted securely, reducing the risk of unauthorized access or data breaches.
What are some common encryption protocols used to secure communication channels?
Common encryption protocols used to secure communication channels include HTTPS (Hypertext Transfer Protocol Secure) and SSL/TLS (Secure Sockets Layer/Transport Layer Security), which encrypt data exchanged between a user's browser and a website.
![The 5 Best Laptops for Small Businesses in 2024 [All Budgets]](https://business.blogcristiano.net/wp-content/uploads/2025/11/Top-5-Tech-Gadgets-for-Entrepreneurs-75x75.jpg)
![The 5 Best Laptops for Small Businesses in 2024 [All Budgets]](https://business.blogcristiano.net/wp-content/uploads/2025/11/Top-5-Tech-Gadgets-for-Entrepreneurs-120x86.jpg)